75+ pages which of the following is the least secure authentication method 1.9mb. CHAP is more secure than PAP because it encrypts usernames and passwords. B Size of the chroot jail. Username and password is the least secure method of authentication in comparison of smart card and biometrics authentication. Read also secure and understand more manual guide in which of the following is the least secure authentication method Passwords can be compromised more easily than to replicate a physical thing like key card fingerprint or retina.
A 19thAugust88 b Delhi88 c Passw0rd. Kerberos can reduce page latency in certain scenarios or increase the number of pages that a front-end web server can serve in certain scenarios.

Microsoft S Maverick Mission Against Malware Infographic Microsoft Inter Technology Malware Malwareanal Online Infographic Cyber Safety Cyber Security
| Title: Microsoft S Maverick Mission Against Malware Infographic Microsoft Inter Technology Malware Malwareanal Online Infographic Cyber Safety Cyber Security |
| Format: ePub Book |
| Number of Pages: 138 pages Which Of The Following Is The Least Secure Authentication Method |
| Publication Date: May 2021 |
| File Size: 6mb |
| Read Microsoft S Maverick Mission Against Malware Infographic Microsoft Inter Technology Malware Malwareanal Online Infographic Cyber Safety Cyber Security |
 |
If a biometric is stored improperly such as on the cloud it can become a shared secret and subject to leaks.

More common in the business environment. Which of the following is NOT true of Open System Authentication OSA. Which of the following is the least secure method of authentication. Anonymous authentication does not provide security as a user can log on to the system anonymously and he is. 8 Which of the following is not an authorization type. Which of the following is not a CERT security practice a.
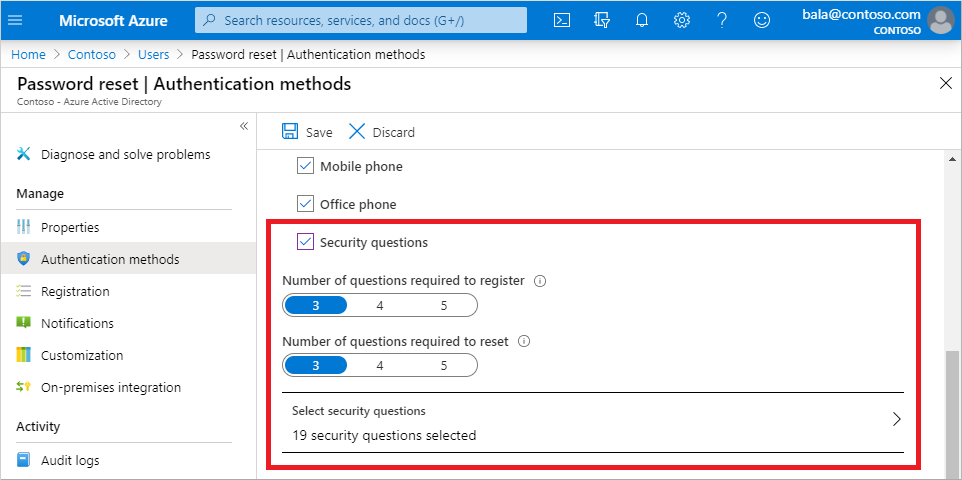
Security Questions Authentication Method Azure Active Directory Microsoft Docs
| Title: Security Questions Authentication Method Azure Active Directory Microsoft Docs |
| Format: eBook |
| Number of Pages: 221 pages Which Of The Following Is The Least Secure Authentication Method |
| Publication Date: April 2018 |
| File Size: 2.3mb |
| Read Security Questions Authentication Method Azure Active Directory Microsoft Docs |
 |

New Police Radars Can See Inside Homes Police Radar Cool Tech
| Title: New Police Radars Can See Inside Homes Police Radar Cool Tech |
| Format: eBook |
| Number of Pages: 144 pages Which Of The Following Is The Least Secure Authentication Method |
| Publication Date: April 2017 |
| File Size: 3.4mb |
| Read New Police Radars Can See Inside Homes Police Radar Cool Tech |
 |

On Infographics
| Title: On Infographics |
| Format: ePub Book |
| Number of Pages: 186 pages Which Of The Following Is The Least Secure Authentication Method |
| Publication Date: January 2017 |
| File Size: 1.7mb |
| Read On Infographics |
 |

5 Fast And Easy Ways To Secure Your Mobile Device Infographic Educational Infographic Infographic Infographic Marketing
| Title: 5 Fast And Easy Ways To Secure Your Mobile Device Infographic Educational Infographic Infographic Infographic Marketing |
| Format: PDF |
| Number of Pages: 163 pages Which Of The Following Is The Least Secure Authentication Method |
| Publication Date: June 2021 |
| File Size: 725kb |
| Read 5 Fast And Easy Ways To Secure Your Mobile Device Infographic Educational Infographic Infographic Infographic Marketing |
 |

Data Security Privacy Global Insights Visual Ly Data Security Loyalty Card Program Cyber Security
| Title: Data Security Privacy Global Insights Visual Ly Data Security Loyalty Card Program Cyber Security |
| Format: eBook |
| Number of Pages: 322 pages Which Of The Following Is The Least Secure Authentication Method |
| Publication Date: March 2019 |
| File Size: 2.1mb |
| Read Data Security Privacy Global Insights Visual Ly Data Security Loyalty Card Program Cyber Security |
 |

On Tech News
| Title: On Tech News |
| Format: ePub Book |
| Number of Pages: 291 pages Which Of The Following Is The Least Secure Authentication Method |
| Publication Date: July 2019 |
| File Size: 2.1mb |
| Read On Tech News |
 |

Guide To Wordpress Brute Force Attacks Wordpress Wordpress Security Attack
| Title: Guide To Wordpress Brute Force Attacks Wordpress Wordpress Security Attack |
| Format: ePub Book |
| Number of Pages: 311 pages Which Of The Following Is The Least Secure Authentication Method |
| Publication Date: December 2017 |
| File Size: 2.1mb |
| Read Guide To Wordpress Brute Force Attacks Wordpress Wordpress Security Attack |
 |

Security Awareness Tips Cyber Security Awareness Security Panies Cyber Security
| Title: Security Awareness Tips Cyber Security Awareness Security Panies Cyber Security |
| Format: ePub Book |
| Number of Pages: 150 pages Which Of The Following Is The Least Secure Authentication Method |
| Publication Date: August 2021 |
| File Size: 6mb |
| Read Security Awareness Tips Cyber Security Awareness Security Panies Cyber Security |
 |

On Semiconductor Market Research Report
| Title: On Semiconductor Market Research Report |
| Format: eBook |
| Number of Pages: 139 pages Which Of The Following Is The Least Secure Authentication Method |
| Publication Date: April 2020 |
| File Size: 3.4mb |
| Read On Semiconductor Market Research Report |
 |

How Does Passwordless Authentication Work Security Wiki
| Title: How Does Passwordless Authentication Work Security Wiki |
| Format: ePub Book |
| Number of Pages: 172 pages Which Of The Following Is The Least Secure Authentication Method |
| Publication Date: July 2018 |
| File Size: 1.8mb |
| Read How Does Passwordless Authentication Work Security Wiki |
 |

Authentication Method An Overview Sciencedirect Topics
| Title: Authentication Method An Overview Sciencedirect Topics |
| Format: eBook |
| Number of Pages: 333 pages Which Of The Following Is The Least Secure Authentication Method |
| Publication Date: June 2021 |
| File Size: 800kb |
| Read Authentication Method An Overview Sciencedirect Topics |
 |
More common in the business environment. Which of the following is a strong password. Adaptive Multi-Factor Authentication MFA Part of deploying a secure authentication method means understanding the risks posed by each factor and combining them effectively to mitigate those risks.
Here is all you need to read about which of the following is the least secure authentication method Username and password can be intercepted. The data breaches companies like Adobe Equifax and Yahoo faced are examples of what happens when organizations fail to secure their user authentication. Eavesdropping can be countered by using encryption. 5 fast and easy ways to secure your mobile device infographic educational infographic infographic infographic marketing security awareness tips cyber security awareness security panies cyber security how does passwordless authentication work security wiki on semiconductor market research report on tech news guide to wordpress brute force attacks wordpress wordpress security attack Username and password is the least secure method of authentication.